Multi-Layer Authentication with Neural Biometrics for Secure Client-Side File Encryption
DOI:
https://doi.org/10.26438/ijcse/v13i11.1320Keywords:
Neural biometrics, AES-256-GCM, PBKDF2-SHA256, Client-side encryption, WebAuthn, Face and iris recognition, Offline data security, Deep learning, Data privacyAbstract
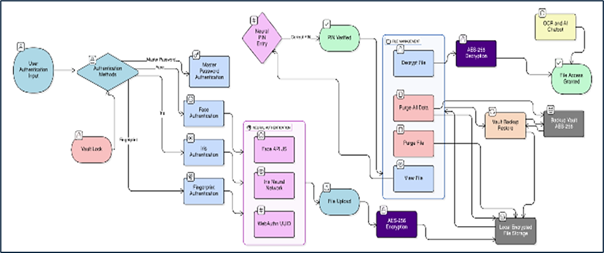
Secure local data storage is increasingly important as cloud-based systems remain vulnerable to breaches and surveillance. This paper presents an offline client-side file security system that combines AES-256-GCM encryption with multi-layer authentication driven by neural biometrics. Face, iris, and fingerprint recognitions are integrated with PBKDF2-SHA256 key derivation. WebAuthn and deep-learning models support fast and accurate validation of biometrics without any external servers. Experimental results have shown that authentication latency remains low, averaging 3.66 ms for face recognition, 2 ms for iris detection, and 3.6 ms for fingerprint verification, thus allowing for smooth real-time operation. It retains full functionality even offline, ensuring a high level of data sovereignty by avoiding cloud exposure risks. In general, this work represents a privacy-first, cross-platform encryption solution to improve the security and usability of neural biometric authentication along with device-level cryptography.
References
[1] Y. Chen, H. Song, and K. Lee, “A deep exploration of BitLocker encryption and security mechanism,” in Proc. IEEE Int. Conf. Trust, Security and Privacy in Computing and Communications (TrustCom), Vol.1, pp.779–785, 2020.
[2] Federal Office for Information Security (BSI), “Security evaluation of VeraCrypt,” Tech. Rep., BSI, pp.1–125, 2016.
[3] M. Zhang, L. Wang, and Y. Chen, “Evaluation of cloud-based encrypted storage systems: Performance and security trade-offs,” IEEE Trans. Cloud Comput., Vol.10, No. 4, pp.1891–1905, 2022.
[4] R. Kaur, A. Jain, and S. Kumar, “Optimization classification of sunflower recognition through machine learning,” Mater. Today: Proc., Vol.51, pp.207–211, 2022.
[5] H. Lee, J. Park, and K. Kim, “Comparative study of biometric modalities for secure authentication: Face vs. fingerprint vs. iris,” Pattern Recognit. Lett., Vol.156, pp.85–92, 2022.
[6] Y. Wang, Z. Liu, and X. Zhang, “Deep learning-based face recognition for authentication systems: Implementation and optimization,” IEEE Trans. Inf. Forensics Secur., Vol.18, pp.2145–2158, 2023.
[7] R. Gupta, S. Mehta, and K. Jain, “Iris recognition using deep convolutional neural networks: A practical implementation,” Expert Syst. Appl., Vol.213, article 118912, 2023.
[8] R. Kaur, A. Jain, P. Saini, and S. Kumar, “A review analysis techniques of flower classification based on machine learning algorithms,” in Proc. 1st Int. Conf. Technol. Smart Green Connected Soc., ECS Trans., Vol.107, No.1, pp.9609–9614, 2021.
[9] M. Johnson, L. Thompson, and A. Williams, “AES-256-GCM encryption for secure file storage: Performance analysis and best practices,” J. Cryptogr. Eng., Vol.12, No.4, pp.421–436, 2022.
[10] A. Jain and R. Kaur, “Flower prediction and classification using machine learning algorithms,” Stochastic Model. Appl., Vol.26, Special Issue.7, pp.329–334, 2022.
[11] D. Chen, H. Wu, and F. Yang, “OCR implementation using Tesseract.js in web applications: Accuracy and performance evaluation,” Int. J. Doc. Anal. Recognit., Vol.25, No.3, pp.267–281, 2022.
[12] K. Patel and R. Shah, “IndexedDB for secure client-side storage: Implementation guidelines and security considerations,” J. Web Eng., Vol.21, No.5, pp.1423–1445, 2022.
[13] T. Brown, M. Davis, and L. White, “Performance evaluation of AES encryption in file storage systems: A benchmarking study,” Comput. Stand. Interfaces, Vol.82, article 103631, 2022.
[14] R. Kaur, A. Jain, P. Saini, and S. Kumar, “A review analysis techniques of flower classification based on machine learning algorithms,” ECS Trans., Vol.107, No.1, pp.9609, 2022.
[15] S. Kumar, K. Singh, and P. Sharma, “PBKDF2 key derivation in web applications: Security analysis and implementation,” Cryptography, Vol.6, No.4, article 58, 2022.
[16] T. Anderson, M. Brown, and K. Wilson, “Auto-lock mechanisms in secure applications: Balancing security and usability,” Comput. Secur., Vol.118, article 102734, 2022.
[17] N. Sharma, P. Verma, and A. Kumar, “Comparative evaluation of local vs. cloud storage encryption systems,” J. Netw. Comput. Appl., Vol.205, article 103456, 2022.
[18] S. Goyal and A. Saini, “A study of advanced encryption tools for data security: AxCrypt, VeraCrypt, and BitLocker,” Int. J. Comput. Appl., Vol.134, No.17, pp.23–27, 2016.
[19] M. Thompson, L. Davis, and R. Miller, “Neural PIN implementation for enhanced security in biometric systems,” Int. J. Biometrics, Vol.14, No.3/4, pp.312–328, 2022.
[20] A. Panwar, R. Kaur, A. Bamba, and D. Bedi, “A comprehensive review of speech emotion recognition systems,” Int. J. Sci. Res. Eng. Manag., Vol.9, No.5, 2025.
[21] P. Singh, K. Kumar, and M. Sharma, “Advantages of client-side encryption over server-side: A security and privacy analysis,” IEEE Secur. Privacy, Vol.20, No.4, pp.56–64, 2022.
[22] Y. Chen, X. Liu, and W. Zhang, “Why multi-modal biometrics outperforms single-modal: A comprehensive analysis,” ACM Comput. Surv., Vol.55, No. 3, article 52, pp.25, 2023.
[23] R. Kaur and S. Porwal, “An optimized computer vision approach to precise well-bloomed flower yielding prediction using image segmentation,” Int. J. Comput. Appl., Vol.119, No.23, 2015.
[24] R. Williams, S. Johnson, and T. Anderson, “Zero-knowledge architecture in secure applications: Benefits and implementation,” J. Cybersecur. Privacy, Vol.3, No.1, pp.1–18, 2023.
[25] B. Lee, K. Kim, and C. Park, “Advantages of AES-256-GCM over other encryption modes for file storage,” J. Inf. Secur. Appl., Vol.66, article 103156, 2022.
[26] R. Kaur and D. Jain, “Flower prediction and classification using machine learning algorithms,” Stochastic Modeling, Vol.69, No.70, pp.63–4658, 2022.
[27] M. Garcia, L. Martinez, and J. Rodriguez, “Local storage vs. cloud storage: Security and privacy advantages,” Comput. Secur., Vol.121, article 102845, 2022.
[28] R. Kaur, A. Jain, and S. Kumar, “Optimization classification of sunflower recognition through machine learning,” Mater. Today: Proc., Vol.51, pp.207–211, 2022.
[29] S. Kumar, P. Patel, and R. Singh, “Face recognition advantages over traditional password authentication: Usability and security perspective,” Human-centric Comput. Inf. Sci., Vol.12, article 45, 2022.
[30] K. Wilson, M. Thompson, and A. Davis, “Why iris recognition provides superior accuracy: A comparative biometric study,” IEEE Trans. Pattern Anal. Mach. Intell., Vol.45, No. 3, pp.3456–3471, 2023.
[31] H. Patel, K. Sharma, and N. Kumar, “Advantages of progressive web apps for secure applications: Performance and security analysis,” J. Web Eng., Vol.21, No. 6, pp.1789–1812, 2022.
[32] Rupinder Kaur, “Yield prediction precision of rose flower recognition using segmentation,” Int. J. Eng. Technol. Comput. Res., Vol.3, No.2, pp.31–33, 2015.
[33] T. Zhang, Y. Wang, and L. Chen, “Real-time biometric authentication advantages: Balancing security and user experience,” ACM Trans. Privacy Secur., Vol.26, No. 2, article 15, pp.28, 2023.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution 4.0 International License.
Authors contributing to this journal agree to publish their articles under the Creative Commons Attribution 4.0 International License, allowing third parties to share their work (copy, distribute, transmit) and to adapt it, under the condition that the authors are given credit and that in the event of reuse or distribution, the terms of this license are made clear.




