A Model for Enhancing Security and Privacy in Pervasive Computing using Homomorphic Encryption
DOI:
https://doi.org/10.26438/ijcse/v13i8.2129Keywords:
Cryptography, Homomorphic Encryption, Elliptic Curve CryptographyAbstract
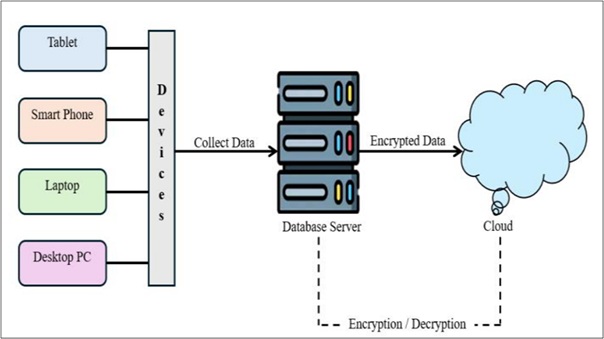
Pervasive computing seamlessly integrates computational capabilities into everyday environments, enhancing user experiences while simultaneously exposing systems to critical security and privacy risks. These vulnerabilities such as unauthorized access, data interception, and exploitation of device-level weaknesses demand encryption methods capable of preserving data confidentiality even during active computation. This paper proposed a novel security model built on Fully Homomorphic Encryption (FHE), enabling operations on encrypted information without decryption, thus ensuring privacy during its lifecycle. The model is structured into a four layered architecture comprising of data collection, encryption, encrypted computation (cloud/edge), and decryption. The study utilized Brakerski/Fan-Vercauteren (BFV) scheme and implemented it using Microsoft SEAL library with VB.NET and C++ for secure, exact integer arithmetic. An experimental evaluation was conducted across 10 to 50 simulated devices using synthesized smart environment data. Experimental finding showed developed model achieved a security accuracy of 95.8%, privacy loss of just 0.6%, and a processing overhead of 720ms, confirming its effectiveness and scalability. To further validate the performance of the developed HE model, a detailed comparative analysis was conducted against that of the traditional cryptographic techniques including AES, RSA, and ECC. While the developed HE model incurs higher computational overhead, it outperformed all baseline methods in terms of security accuracy and privacy preservation. Specifically, the developed HE model showed the lowest privacy leakage and highest resistance to unauthorized access, making it more suitable for sensitive applications despite the trade-off in processing speed. The empirical results highlight the model’s strong potential for deployment in real-world domains such as smart cities, healthcare systems, and the Internet of Things (IoT). However, future work should focus on optimizing the model through hybrid FHE–lightweight encryption combinations and integration with real-time IoT protocols.
References
[1] J. Agarkhed, G. Pawar, "Enhanced Security Model for Pervasive Computing Using Machine Learning Techniques," In the Preceeding of the 3rd International Conference on Integrated Intelligent Computing Communication & Security (ICIIC 2021), pp.414-420, 2021.
[2] Y. Jiang, M. A. Rezazadeh Baee, L. R. Simpson, P. Gauravaram, J. Pieprzyk, T. Zia, et al., "Pervasive user data collection from cyberspace: Privacy concerns and countermeasures," Cryptography, Vol.8, Issue.5, pp.1-5, 2024.
[3] K. M. Pradhan, "Pervasive Computing: A New Horizons," International Journal of Computer Science and Engineering, Vol.7, pp.1137-1140, 2019.
[4] M. A. I. Mallick, R. Nath, "Navigating the cyber security landscape: A comprehensive review of cyber-attacks, emerging trends, and recent developments," World Scientific News, Vol.190, pp.1-69, 2024.
[5] E. I. Egho-Promise, M. Sitti, "Big data security management in digital environment," American Journal of Multidisciplinary Research & Development (AJMRD), Vol.6, pp.01-34, 2024.
[6] M. Abudalou, "Enhancing Data Security through Advanced Cryptographic Techniques," Int. J. Comput. Sci. Mob. Comput., Vol.13, pp.88-92, 2024.
[7] E. Mollakuqe, A. Parduzi, S. Rexhepi, V. Dimitrova, S. Jakupi, R. Muharremi, et al., "Applications of Homomorphic Encryption in Secure Computation," Open Research Europe, Vol.4, pp.158, 2024.
[8] C. Marcolla, V. Sucasas, M. Manzano, R. Bassoli, F. H. Fitzek, N. Aaraj, "Survey on fully homomorphic encryption, theory, and applications," In the Proceedings of the 2022 IEEE International Conference," Vol.110, pp.1572-1609, 2022.
[9] W. Ren, X. Tong, J. Du, N. Wang, S. C. Li, G. Min, et al., "Privacy-preserving using homomorphic encryption in Mobile IoT systems," Computer Communications, Vol.165, pp.105-111, 2021.
[10] O. Taylor, P. Asagba, B. Eke, "A Consensus-Aware Pervasive Computing Systems Model for Smart Space Environments," Journal of Advances in Mathematical & Computational Sciences, Vol.7, pp.1-8, 2019.
[11] I. N. Davies, O. E. Taylor, V. I. E. Anireh, E. O. Bennett, "Adaptive Hybrid Case-Based Neuro-Fuzzy Model for Intrusion Detection and Prevention for Smart Home Network," International Journal of Computer Sciences and Engineering, Vol.10, pp.01-10, 2024.
[12] O. E. Taylor, I. N. Davies, "A Framework for Human Computer Interaction (HCI) in Pervasive Learning Environment," International journal of Computer Applications, Vol.187, pp.26-33, 2025.
[13] S. Zubair, H. M. Ahmed, "An In-Depth Comparative Analysis of Cryptographic Techniques for Ensuring Data Privacy in E-Applications," Paper Presented at the 2024 3rd International Conference for Advancement in Technology (ICONAT), pp.1-8, 2024.
[14] S. Kumar, S. K. Singh, B. B. Gupta, K. Psannis, J. Wu, "Homomorphic Encryption in Smart City Applications for Balancing Privacy and Utility," Innovations in Modern Cryptography, ed: IGI Global, pp.241-269, 2024.
[15] S. Zhu, T. Yu, T. Xu, H. Chen, S. Dustdar, S. Gigan, et al., "Intelligent computing: the latest advances, challenges, and future," Intelligent Computing, Vol.2, pp.6-10, 2023.
[16] O. Layode, H. N. N. Naiho, G. S. Adeleke, E. O. Udeh, T. T. Labake, "Data privacy and security challenges in environmental research: Approaches to safeguarding sensitive information," International Journal of Applied Research in Social Sciences, Vol.6, pp.1193-1214, 2024.
[17] O. E. Taylor, V. T. Emmah, "Comparative Analysis of Cryptographic Algorithms in Securing Data," International Journal of Engineering Trends and Technology, Vol.58, pp.118-122, 2018.
[18] A. H. K. Roseline, N. D. Nwiabu, O. E. Taylor, V. Anireh, "Solving Time Complexity Issues in Storage Area Network using Enhanced Homomorphic Encryption," International Journal of Computer Science and Mathematical Theory (IJCSMT), Vol.10, pp.73-82, 2024.
[19] R. R. Asaad, S. R. Zeebaree, "Enhancing Security and Privacy in Distributed Cloud Environments: A Review of Protocols and Mechanisms," Academic Journal of Nawroz University, Vol.13, pp.476-488, 2024.
[20] M. A. Jalil, "Enhancing Privacy in Artificial Intelligence Services Using Hybrid Homomorphic Encryption," Babylonian Journal of Artificial Intelligence, Vol.2024, pp.168-174, 2024.
[21] K. Nguyen, M. Budzys, E. Frimpong, T. Khan, A. Michalas, "A Pervasive, Efficient and Private Future: Realizing Privacy-Preserving Machine Learning Through Hybrid Homomorphic Encryption," In the Preceeding of the 2024 IEEE Conference on Dependable, Autonomic and Secure Computing (DASC), pp.47-56, 2024.
[22] M. Abutaha, B. Atawneh, L. Hammouri, G. Kaddoum, "Secure lightweight cryptosystem for IoT and pervasive computing," Scientific Reports, Vol.12, pp.19649, 2022.
[23] C. Mendoza, J. Herrera, "Enhancing Security and Privacy in Advanced Computing Systems: A Comprehensive Analysis," Journal of Advanced Computing Systems, Vol.3, pp.1-9, 2023.
[24] I. Davies, O. Taylor, V. Anireh, E. Bennett, "Node-Level Privacy Preservation Mechanism in Internet-of-Things Network using Elliptic Curve Cryptography," Journal of Applied Computer Science & Mathematics, Vol.18, pp.26-36, 2024.
[25] O. Taylor, C. Igiri, "Enhancing Image Encryption using Histogram Analysis, Adjacent Pixel Autocorrelation Test in Chaos-based Framework," International Journal of Computer Applications, Vol.186, pp.9-18, 2024.
[26] A. Murugesan, B. Saminathan, F. Al?Turjman, R. L. Kumar, "Analysis on homomorphic technique for data security in fog computing," Transactions on Emerging Telecommunications Technologies, Vol.32, pp.3990, 2021.
[27] E. Okpu, O. Taylor, "Analysing the Integration of AES-256 Encryption and HMAC Hashing in IoT Smart Healthcare Systems," Ci-STEM Journal of Digital Technologies and Expert Systems, Vol.2, pp.18-24, 2025.
[28] A. K. Y. Yanamala, S. Suryadevara, "Adaptive Middleware Framework for Context-Aware Pervasive Computing Environments," International Journal of Machine Learning Research in Cybersecurity and Artificial Intelligence, Vol.13, pp.35-57, 2022.
[29] S. Bansal, D. Kumar, "IoT ecosystem: A survey on devices, gateways, operating systems, middleware and communication," International Journal of Wireless Information Networks, Vol.27, pp.340-364, 2020.
[30] R. Nayak, U. Ghugar, P. Gupta, S. Dash, N. Gupta, "Data Privacy and Compliance in Information Security," Securing the Digital Frontier: Threats and Advanced Techniques in Security and Forensics, pp.17-33, 2025.
[31] D. Hahn, A. Munir, V. Behzadan, "Security and privacy issues in intelligent transportation systems: Classification and challenges," IEEE Intelligent Transportation Systems Magazine, Vol.13, pp.181-196, 2019.
[32] P. N. Swanzy, A. M. Abukari, E. D. Ansong, "Data security framework for protecting data in transit and data at rest in the cloud," Current Journal of Applied Science and Technology, Vol.43, pp.61-77, 2024.
[33] J. Zhang, B. Chen, Y. Zhao, X. Cheng, F. Hu, "Data security and privacy-preserving in edge computing paradigm: Survey and open issues," IEEE Access, Vol.6, pp.18209-18237, 2018.
[34] C. Wang, Y. Wang, Y. Chen, H. Liu, J. Liu, "User authentication on mobile devices: Approaches, threats and trends," Computer Networks, Vol.170, pp.107118, 2020.
[35] J. Mohamed, Z. Ibrahim, M. F. M. Fudzee, S. N. Ramli, "Legibility Impact Factor for Shoulder-Surfing Resistant Authentication Scheme by Visual Perception," International Journal of Business and Technology Management, Vol.6, pp.206-213, 2024.
[36] M. Rashid, M. M. Haque, W. Wang, "IoT Complexity: Security, Vulnerabilities and Risks," European Journal of Electrical Engineering and Computer Science, Vol.8, pp.1-9, 2024.
[37] S. Aswathy, A. K. Tyagi, "Privacy Breaches through Cyber Vulnerabilities: Critical Issues, Open Challenges, and Possible Countermeasures for the Future," In the Security and Privacy-Preserving Techniques in Wireless Robotics, ed: CRC Press, pp.163-210, 2022.
[38] S. D. Pasham, "Privacy-preserving data sharing in big data analytics: A distributed computing approach," The Metascience, Vol.1, pp.149-184, 2023.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution 4.0 International License.
Authors contributing to this journal agree to publish their articles under the Creative Commons Attribution 4.0 International License, allowing third parties to share their work (copy, distribute, transmit) and to adapt it, under the condition that the authors are given credit and that in the event of reuse or distribution, the terms of this license are made clear.




