An Integrated Approach to Optimize the Intrusion Detection System in SDN based on Feature Selection and Deep Learning Techniques
DOI:
https://doi.org/10.26438/ijcse/v13i5.916Keywords:
Software Defined Networking (SDN),, Software Defined Networking (SDN), Outlier, Feature EngineeringAbstract
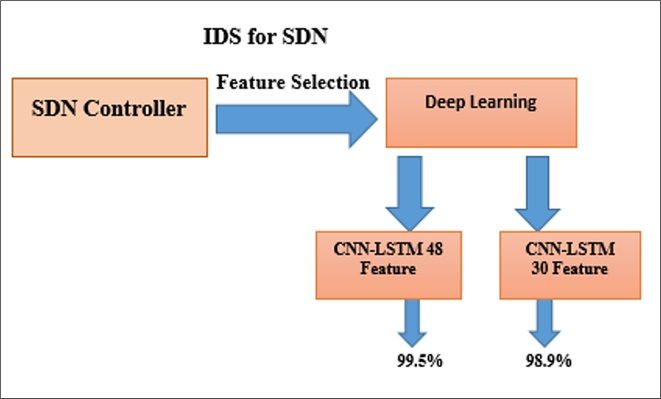
Software-defined networking (SDN) is a revolutionary innovation that has become known as an internet architecture. It allows for modular, adaptable, and effective network management alternatives by decoupling the management plane about the data plane. The centralized management and open interfaces that are present in software-defined networking (SDN) provide a number of new security issues, the most notable of which is the increased danger of network breaches. It is difficult for traditional security measures to adjust to the dynamic and programmable nature of SDN, which is why more intelligent solutions are required. The ability of deep learning (DL)-based intrusion detection systems (IDS) to acquire knowledge from data and distinguish complex attack trends in real time has led to their rising popularity. This research looks at software-defined networking (SDN) environments with intrusion detection systems (IDS) built on deep learning algorithms. Identify outliers, feature selection and architectures approaches are discussed. We have constructed and compared two models based on feature selection for comprehensive Intrusion Detection System (IDS) solution. One of these models uses CNN-LSTM architecture, using 48 features achieved the maximum accuracy, which was 99.5%. On the other hand, the CNN-LSTM model using 30 features achieved 98.9% accuracy.
References
[1] A. Kaur, C. R. Krishna, and N. V. Patil, “A comprehensive review on Software-Defined Networking (SDN) and DDoS attacks: Ecosystem, taxonomy, traffic engineering, challenges and research directions,” Computer Science Review, Vol.55, pp.100692, 2025.
[2] D.?S.?N.?Wijesekara and P. Arachchige, “Intrusion detection using blockchain in Software Defined Networking: A literature review,” Journal of Engineering Science & Technology Review, Vol.18, No.1,?2025.
[3] A. Vijayan and A. Anitha, “A review of intrusion detection systems in Software Defined Networks,” in Proc.?2025 Int. Conf. Electronics and Renewable Systems?(ICEARS), Feb., pp.859–864, 2025.
[4] A.?H. Janabi, T. Kanakis, and M. Johnson, “Survey: Intrusion Detection System in Software Defined Networking,” IEEE Access, Vol.12, pp.164097–164120,?2024.
[5] A.?O. Salau and M.?M. Beyene, “Software defined networking based network traffic classification using machine learning techniques,” Scientific Reports, Vol.14, No.1, 2024.
[6] D. Nuñez Agurto, W. Fuertes, L. Marrone, E. Benavides Astudillo, C. Coronel Guerrero, and F. Perez, “A novel traffic classification approach by employing deep learning on Software Defined Networking,” Future Internet, Vol.16, No.5, 2024.
[7] F. Ahmed, I.?A. Sumra, and U. Jamil, “A comprehensive review on DDoS attack in Software Defined Network (SDN): Problems and possible solutions,” Journal of Computing & Biomedical Informatics, Vol.7, No.1, pp.353–363,?2024.
[8] M. Zhong, M. Lin, C. Zhang, and Z. Xu, “A survey on graph neural networks for intrusion detection systems: Methods, trends and challenges,” Computers & Security, Vol.141, 2024.
[9] H. Sat?lmi?, S. Akleylek, and Z.?Y. Tok, “A systematic literature review on host based intrusion detection systems,” IEEE Access, Vol.12, pp.27237–27266,?2024.
[10] D. Srivastava, V. Sharma, P. Kumar, and Y.?K. Sharma, “A comparative analysis of liver cancer detection using neural network algorithm and correlation algorithm,” in Proc.?2nd Int. Conf. Computational and Characterization Techniques in Engineering & Sciences?(IC3TES), Nov., pp.1–5, 2024.
[11] R.?A. Abed, E.?K. Hamza, and A.?J. Humaidi, “A modified CNN IDS model for enhancing the efficacy of intrusion detection system,” Measurement: Sensors, Vol.35, 2024.
[12] D. Srivastava et?al., “Deep ensemble model for sequence based prediction of PPI: Self improved optimization assisted intelligent model,” Multimedia Tools and Applications, Vol.83, No.26, pp.68135–68154,?2024.
13] F. Zhao, H. Li, K. Niu, J. Shi, and R. Song, “Application of deep learning based intrusion detection system (IDS) in network anomaly traffic detection,” Applied and Computational Engineering, Vol.86, pp.231–237,?2024.
[14] J. Arevalo Herrera, J. Camargo Mendoza, J.?I. Martínez Torre, T. Zona Ortiz, and J.?M. Ramirez, “Assessing SDN controller vulnerabilities: A survey on attack typologies, detection mechanisms, controller selection, and dataset application in machine learning,” Wireless Personal Communications, Vol.140, No.1, pp.739–775,?2025.
[15] N. Mostafa, K. Metwally, and K. Badran, “Survey on SDN based intrusion detection systems,” in Proc.?14th Int. Conf. Electrical Engineering?(ICEENG), May, pp.317–322, 2024.
[16] M. Chouikik, M. Ouaissa, M. Ouaissa, Z. Boulouard, and M. Kissi, “Detection and mitigation of DDoS attacks in SDN based intrusion detection system,” Bulletin of Electrical Engineering and Informatics, Vol.13, No.4, pp.2750–2757,?2024.
[17] A. Chetouane and K. Karoui, “New continual federated learning system for intrusion detection in SDN based edge computing,” Concurrency and Computation: Practice and Experience, Vol.37, No.2, 2025.
[18] S. M’Rabet, H. Sahli, B. Yorobi, and M. Sayadi, “An inventive network intrusion detection system: Composite deep learning CNN LSTM model,” in Proc.?IEEE 6th Int. Conf. Image Processing, Applications and Systems?(IPAS), Jan., pp.1–6, 2025.
[19] U.?K. Addanki, R.?B. Devareddi, K.?K. Kamarajugadda, M. Pavani, and P. Gera, “Machine learning powered intrusion detection system for Agriculture 4.0: Securing the next generation of farming,” International Journal of Innovative Research and Scientific Studies, Vol.8, No.1, pp.1964–1978,?2025.
[20] V. Sharma, L. Kumar, and D. Srivastava, “Machine learning based prediction of users’ involvement on social media,” in Advanced Applications of NLP and Deep Learning in Social Media Data, Hershey,?PA, USA: IGI Global,?pp.151–170, 2023.
[21] V. Sharma, D. Srivastava, L. Kumar, M. Payal, and M.?S. Adhikari, “Machine learning based image compression by reducing dimensionality,” preprint, Feb.?2024.
[22] R. Arthi, S. Krishnaveni, and S. Zeadally, “An intelligent SDN IoT enabled intrusion detection system for healthcare systems using a hybrid deep learning and machine learning approach,” China Communications, pp.1–21,?2024.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution 4.0 International License.
Authors contributing to this journal agree to publish their articles under the Creative Commons Attribution 4.0 International License, allowing third parties to share their work (copy, distribute, transmit) and to adapt it, under the condition that the authors are given credit and that in the event of reuse or distribution, the terms of this license are made clear.




