Quantum Safe Cryptography using Modern Hybrid Cryptography Techniques to Secure Data
DOI:
https://doi.org/10.26438/ijcse/v13i4.4758Keywords:
Hybrid Cryptosystems,, Advanced Encryption Standard, Symmetric Key Encryptio, Asymmetric Key Encryption,, Quantum Safe Cryptography, Quantum Key Distribution, Post-Quantum Cryptography, Lattice-Based CryptographyAbstract
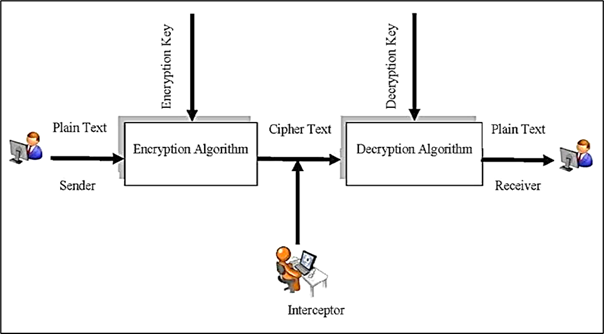
Cryptography, the practice of concealing messages for private exchange, has evolved significantly to address the challenges posed by new communication methods. In today`s digital world, cryptography has become the cornerstone of cybersecurity, using advanced mathematics like number theory and computational complexity to protect digital information through algorithms. The upcoming arrival of quantum computers poses a serious threat to traditional cryptographic methods, especially those based on asymmetric key cryptography. Quantum Safe Cryptography (QSC) represents the next step in information security, designed to develop cryptographic systems that can withstand attacks from both quantum and classical computers. As quantum computing moves from theory to reality, it`s becoming clear that current cryptographic methods based on integer factorization and discrete logarithm problems are vulnerable to quantum algorithms like Shor`s algorithm. This study highlights the security risks that quantum computing poses to existing encryption methods and proposes a comprehensive approach to quantum-safe cryptography. The transition to quantum-resistant algorithms involves replacing vulnerable cryptographic systems with alternatives that can resist quantum computational attacks. Current analysis shows that while asymmetric key cryptography faces immediate vulnerability, symmetric key algorithms and hash functions remain relatively secure in the near term with appropriate adjustments. Quantum cryptography, which directly uses quantum mechanical principles, offers highly secure encryption mechanisms, notably Quantum Key Distribution (QKD). This research aims to enhance the security of digital infrastructure against quantum threats by evaluating hybrid cryptographic implementations that combine classical and quantum-resistant approaches for optimal security.
References
[1] B. Schneier, Applied Cryptography: Protocols, Algorithms, and Source Code in C, 20th Anniversary Edition. Wiley, 2015.
[2] S. Singh, The Code Book: The Science of Secrecy from Ancient Egypt to Quantum Cryptography. Anchor Books, 2011.
[3] NIST, "Communications Security," NIST Computer Security Resource Center, Feb. 2024.
[4] J. Watrous, "Practical introduction to quantum-safe cryptography," IBM Quantum Learning, 2023.
[5] D. Clemon and V. Velasquez, "Quantum Computing: Definition, How It`s Used, and Example," Investopedia, Feb. 2024.
[6] L. Chen et al., "Report on Post-Quantum Cryptography," NIST Internal Report 8105, Apr. 2021.
[7] M. Ajtai and C. Dwork, "A public-key cryptosystem with worst-case/average-case equivalence," in Proceedings of the 29th Annual ACM Symposium on Theory of Computing, pp.284-293, 1997.
[8] P. W. Shor, "Algorithms for quantum computation: Discrete logarithms and factoring," in Proceedings of the 35th Annual Symposium on Foundations of Computer Science, pp.124-134, 1994.
[9] D. J. Bernstein and T. Lange, "Post-quantum cryptography," Nature, Vol.549, No.7671, pp.188-194, 2017.
[10] M. Khalid Yousif, Z. E. D. S. W. K., "Information security for big data using the NTRUEncrypt method," Measurement: Sensors, pp.1-5, 2023.
[11] G. S. Bhathal and A. Singh, "Big data computing with distributed computing frameworks," in Innovations in Electronics and Communication Engineering: Proceedings of the 7th ICIECE 2018, 2018.
[12] J. Singh and G. S. Bhathal, "A Review on Storage Security Challenges in Cloud Computing," International Journal of Advanced Research in Computer Science and Software Engineering, pp.225-228, 2015.
[13] W. Stallings, Cryptography and Network Security: Principles and Practice, 8th Edition. Pearson, 2023.
[14] G. K. Sandhu and G. S. Bhathal, "To Enhance the OTP Generation Process for Cloud Data Security using Diffie-Hellman and HMAC," Global Journal of Computer Science and Technology, 2016.
[15] D. Boneh and V. Shoup, A Graduate Course in Applied Cryptography, Version 0.6, 2023.
[16] A. J. Menezes, P. C. Van Oorschot, and S. A. Vanstone, Handbook of Applied Cryptography. CRC Press, 2018.
[17] M. Campagna et al., "Quantum Safe Cryptography and Security," European Telecommunications Standards Institute, France, 2015.
[18] L. K. Grover, "A fast quantum mechanical algorithm for database search," in Proceedings of the 28th Annual ACM Symposium on Theory of Computing, pp.212-219, 1996.
[19] D. J. Bernstein, J. Buchmann, and E. Dahmen, Post-Quantum Cryptography. Springer, 2009.
[20] R. Agrawal, M. Singh, and D. Agrawal, "Quantum resistant security solutions for blockchain technology," Journal of Physics: Conference Series, Vol.1831, No.1, 2021.
[21] E. Barker, "Recommendation for Key Management: Part 1 – General," NIST Special Publication 800-57 Part 1 Revision 5, May 2020.
[22] NIST, "Post-Quantum Cryptography Standardization," 2024.
[23] Y. Zhao, R. Steinfeld, and A. Sakzad, "FACCT: FAst, Compact, and Constant-Time Discrete Gaussian Sampler over Integers," IEEE Transactions on Computers, Vol.69, No.1, pp.126-137, 2020.
[24] N. P. Smart, "Post-quantum secure cryptographic infrastructures," National Cyber Security Centre, UK, Technical Report, Jan. 2024.
[25] H. Nejatollahi, N. Dutt, S. Ray, F. Regazzoni, I. Banerjee, and R. Cammarota, "Post-Quantum Lattice-Based Cryptography Implementations: A Survey," ACM Computing Surveys, Vol.51, No.6, pp.129:1-129:41, 2024.
[26] M. Braithwaite, "Experimenting with Post-Quantum Cryptography," Google Security Blog, Jul. 2021.
[27] D. Moody et al., "Status Report on the Third Round of the NIST Post-Quantum Cryptography Standardization Process," NIST Interagency Report 8413, Jul. 2022.
[28] T. Lange and C. van Vredendaal, "Practical Post-Quantum Cryptography," IEEE Security & Privacy, Vol.21, No.1, pp.30-38, 2023.
[29] European Union Agency for Cybersecurity (ENISA), "Post-Quantum Cryptography: Current State and Quantum Mitigation," Report, Jan. 2024.
[30] National Security Agency, "Commercial National Security Algorithm Suite 2.0," Jan. 2024.
[31] N. Sendrier, "Code-based cryptography: State of the art and perspectives," IEEE Security & Privacy, Vol.19, No.1, pp.32-39, 2024.
[32] V. Mavroeidis, K. Vishi, M. D. Zych, and A. Jøsang, "The Impact of Quantum Computing on Present Cryptography," International Journal of Advanced Computer Science and Applications, Vol.9, No.3, 2018.
[33] L. Ducas, E. Kiltz, T. Lepoint, V. Lyubashevsky, P. Schwabe, G. Seiler, and D. Stehlé, "CRYSTALS-Dilithium: A Lattice-Based Digital Signature Scheme," IACR Transactions on Cryptographic Hardware and Embedded Systems, vol.2018, No.1, pp.238-268, 2018.
[34] O. Regev, "On lattices, learning with errors, random linear codes, and cryptography," Journal of the ACM, Vol.56, No.6, pp.1-40, 2009.
[35] J. Hoffstein, J. Pipher, and J. H. Silverman, "NTRU: A ring-based public key cryptosystem," in Algorithmic Number Theory, Springer, pp. 267-288, 1998.
[36] C. Gentry, C. Peikert, and V. Vaikuntanathan, "Trapdoors for hard lattices and new cryptographic constructions," in Proceedings of the 40th Annual ACM Symposium on Theory of Computing, pp. 197-206, 2008.
[37] X. Lu, Y. Liu, D. Jia, H. Xue, J. He, Z. Zhang, Z. Liu, H. Yang, B. Li, and K. Wang, "LAC: Lattice-based Cryptosystems," 2018.
[38] P. Wallden and E. Kashefi, "Cyber security in the quantum era," Communications of the ACM, Vol.62, No.4, pp.120-129, 2019.
[39] J. Daemen and V. Rijmen, The Design of Rijndael: AES - The Advanced Encryption Standard. Springer, 2020.
[40] J. Proos and C. Zalka, "Shor`s discrete logarithm quantum algorithm for elliptic curves," Quantum Information & Computation, Vol.3, No.4, pp.317-344, 2003.
[41] ETSI, "Quantum-Safe Hybrid Key Exchange," ETSI Technical Specification 103 744 V1.1.1, Jan. 2024.
[42] D. Micciancio and O. Regev, "Lattice-based cryptography," in Post-Quantum Cryptography, Springer, pp.147-191, 2009.
[43] A. Hülsing, D. J. Bernstein, C. Dobraunig, M. Eichlseder, S. Fluhrer, S.-L. Gazdag, P. Kampanakis, S. Kölbl, T. Lange, M. M. Lauridsen, F. Mendel, R. Niederhagen, C. Rechberger, J. Rijneveld, and P. Schwabe, "SPHINCS+: Submission to the NIST post-quantum project," 2019.
[44] NIST, "Guidelines for Transitioning to Post-Quantum Cryptography," NIST Special Publication 800-215, Jan. 2024.
[45] M. Mosca, "Cybersecurity in an era with quantum computers: Will we be ready?," IEEE Security & Privacy, Vol.16, No.5, pp.38-41, 2018.
[46] J. H. Cheon, D. Kim, J. Lee, and Y. Song, "Lizard: Cut off the tail! A practical post-quantum public-key encryption from LWE and LWR," in Security and Cryptography for Networks, Springer, pp.160-177, 2018.
[47] T. Prest, P.-A. Fouque, J. Hoffstein, P. Kirchner, V. Lyubashevsky, T. Pornin, T. Ricosset, G. Seiler, W. Whyte, and Z. Zhang, "FALCON: Fast-Fourier Lattice-based Compact Signatures over NTRU," Submission to the NIST Post-Quantum Cryptography Standardization Process, 2019.
[48] A. K. Ekert, "Quantum cryptography based on Bell`s theorem," Physical Review Letters, Vol.67, No.6, pp.661-663, 1991.
[49] C. H. Bennett and G. Brassard, "Quantum cryptography: Public key distribution and coin tossing," in Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, Vol.175, pp.8-12, 1984.
[50] V. Lyubashevsky, L. Ducas, E. Kiltz, T. Lepoint, P. Schwabe, G. Seiler, and D. Stehlé, "CRYSTALS-Kyber: Algorithm Specifications and Supporting Documentation," NIST PQC Round 3 Submission, 2021.
[51] D. J. Bernstein, "Comparing proofs of security for lattice-based encryption," in Selected Areas in Cryptography – SAC 2019, Springer, pp.1-27, 2020.
[52] M. Alagic et al., "Status Report on the Second Round of the NIST Post-Quantum Cryptography Standardization Process," NIST Interagency Report 8309, Jul. 2020.
[53] IEEE, "Quantum Computing Security and Cryptography Standards," IEEE Standard 2041.1-2024, Jan. 2024.
[54] D. Jao and L. De Feo, "Towards quantum-resistant cryptosystems from supersingular elliptic curve isogenies," in Post-Quantum Cryptography, Springer, pp.19-34, 2011.
[55] Cloud Security Alliance, "Practical Implementation of Post-Quantum Cryptography," CSA Research Report, Mar. 2024.
[56] Internet Engineering Task Force (IETF), "Hybrid Post-Quantum Key Encapsulation Methods (PQ KEM) for Transport Layer Security 1.3 (TLS)," Internet-Draft, Jan. 2024.
[57] J. W. Bos, C. Costello, M. Naehrig, and D. Stebila, "Post-quantum key exchange for the TLS protocol from the ring learning with errors problem," in IEEE Symposium on Security and Privacy, pp.553-570, 2015.
[58] R. Steinfeld, "Incremental Transitioning to Post-Quantum Cryptography Through Hybrid Schemes," ACM Transactions on Privacy and Security, Vol.28, No.1, pp.1-42, 2024.
[59] N. Bindel, J. Brendel, M. Fischlin, B. Goncalves, and D. Stebila, "Hybrid Key Encapsulation Mechanisms and Authenticated Key Exchange," in Post-Quantum Cryptography, Springer, pp.206-226, 2023.
[60] European Commission, "Quantum Communication Infrastructure: Transition to Post-Quantum Cryptography," Digital Europe Programme, Technical Report, Jan. 2024.
[61] K. E. Lauter, "The advantages of elliptic curve cryptography for wireless security," IEEE Wireless Communications, Vol.11, No.1, pp.62-67, 2004.
[62] L. Chen, S. Jordan, Y.-K. Liu, D. Moody, R. Peralta, R. Perlner, and D. Smith-Tone, "Report on post-quantum cryptography," NIST Interagency Report 8105, Apr. 2016.
[63] A. Langlois and D. Stehlé, "Worst-case to average-case reductions for module lattices," Designs, Codes and Cryptography, Vol.75, No.3, pp.565-599, 2015.
[64] National Quantum Initiative, "Post-Quantum Cryptography Implementation Guidelines for Critical Infrastructure," Technical Report, Jan. 2024.
[65] C. Peikert, "A decade of lattice cryptography," Foundations and Trends in Theoretical Computer Science, Vol.10, No.4, pp.283-424, 2016.
[66] M. O. Saarinen, "HILA5: On Reliability, Reconciliation, and Error Correction for Ring-LWE Encryption," in Selected Areas in Cryptography – SAC 2017, Springer, pp.192-212, 2018.
[67] World Economic Forum, "Quantum-Safe Cryptography: Strategic Implementation for Global Business," Industry Report, Feb. 2024.
[68] D. Stebila and M. Mosca, "Post-quantum key exchange for the internet and the open quantum safe project," in Selected Areas in Cryptography – SAC 2016, Springer, pp.14-37, 2016.
[69] Google Security Team, "Transitioning to Post-Quantum Cryptography: Lessons from Large-Scale Deployments," Technical White Paper, Jan. 2024.
[70] R. Azarderakhsh, D. Fishbein, and D. Jao, "Efficient implementations of a quantum-resistant key-exchange protocol on embedded systems," Technical Report, University of Waterloo, 2023.
[71] International Telecommunication Union (ITU), "Security architecture for quantum-safe communications," ITU-T Recommendation X.1811, Feb. 2024.
[72] U.S. Department of Defense, "Quantum-Resistant Cryptography Implementation Guide for Defense Systems," Technical Directive, Jan. 2024.
[73] V. Rijmen and J. Daemen, "Advanced Encryption Standard," in Encyclopedia of Cryptography and Security, Springer, pp.31-33, 2011.
[74] Banking and Financial Services Consortium, "Case Study: Quantum-Safe Migration in Global Banking Networks," Industry Report, Jan. 2024.
[75] Healthcare Information and Management Systems Society (HIMSS), "Quantum-Safe Protection for Electronic Health Records: Implementation Case Study," Technical Report, Feb. 2024.
[76] NATO Cyber Defence Centre of Excellence, "Quantum-Resistant Cryptography for Military Applications: Case Studies and Lessons Learned," Technical Report, Jan. 2024.
[77] Global Telecommunications Security Alliance, "5G and 6G Networks: Quantum-Safe Implementation Case Study," Industry Report, Feb. 2024.
[78] Cloud Security Alliance, "Quantum-Safe Cloud Services: Implementation Case Study," Research Report, Jan. 2024.
[79] National Institute of Standards and Technology, "Transitioning to Post-Quantum Cryptography," NIST Special Publication 800-224, Feb. 2024.
[80] World Economic Forum, "Quantum Technology and Cybersecurity: Preparing for the Post-Quantum Era," Global Risk Report, Jan. 2024.
[81] Quantum Economic Development Consortium, "Economic Impact of Quantum Computing on Cybersecurity Infrastructure," Industry Analysis, Feb. 2024.
[82] International Organization for Standardization, "Information Security: Guidelines for Quantum-Safe Cryptography Implementation," ISO/IEC 24485:2024, Jan. 2024.
[83] S. Singh and G. S. Bhathal, "Improving Security and Data Protection of Serverless Computing in the Cloud Environment", International Journal of Computer Sciences and Engineering, Vol.12, Issue.5, pp.19-27, 2024.
[84] J. Singh and G. S. Bhathal, "Securing Multi-Cloud Environment: An Automated Data Deletion System with Integrated Intrusion Detection System Over Multi-Cloud Platforms", International Journal of Computer Sciences and Engineering, Vol.12, Issue.7, pp.33-40, 2024.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution 4.0 International License.
Authors contributing to this journal agree to publish their articles under the Creative Commons Attribution 4.0 International License, allowing third parties to share their work (copy, distribute, transmit) and to adapt it, under the condition that the authors are given credit and that in the event of reuse or distribution, the terms of this license are made clear.




