Encrypting Secret Information inside an Image Using Steganography
DOI:
https://doi.org/10.26438/ijcse/v11i1.1113Keywords:
Encryption, Cryptography, StegnographyAbstract
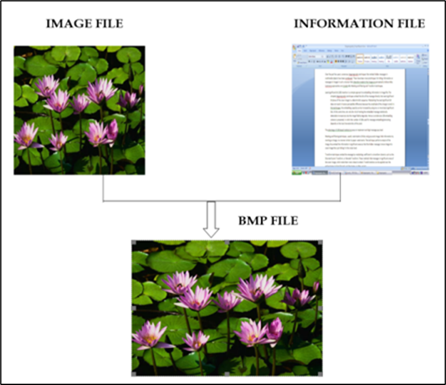
Converting information into the image format has become the latest method which can be implemented for encrypting information into colours. Experts have projected different methods to implement this approach to secure data against hackers. Most of the approaches square measuring readily implemented algorithms or putting forward an easy level of the coding execution which makes these methods a risk to break by attackers. A new and emerging method of operations is discussed through this paper so as to build a word-To-picture encrypting approach. The substitution and transposition operations square measure applied into two levels ((characters (bytes) and bits) of the written information to formulate the secret and safe image. Together the given functions provide lots of strength points to fight against hackers. The projected method has been applied and verified across various sets of information; the recorded observations proved the efficiency and correctness of the methodology as an efficient Text-To-Image encrypting approach.
References
[1]A. Abusukhon, "Block Cipher Encryption for Text-To-Image Algorithm". International Journal of Computer Engineering and Technology (IJCET), Vol.4, Issue.3, 2013.
[2]A. Abusukhon, M. Talib, and H. Almimi, "Distributed Text-to-Image Encryption Algorithm". International Journal of Computer Applications, Vol. 106, No. 1, 2014.
[3]M. Chen, N. Memon, E.K. Wong, Data hiding in document images, in: H. Nemati (Ed.). Premier Reference Source– Information Security and Ethics: Concepts, Methodologies, Tools and Applications, New York: Information Science Reference, pp.438-450, 2008.
[4]D.C. Lou, J.L. Liu, H.K. Tso, Evolution of information ? hiding technology, in H. Nemati (Ed.), Premier Reference Source–Information Security and Ethics: Concepts, Methodologies, Tools and Applications, New York: Information Science Reference, pp.438-450, 2008.
[5]Morkel T. , Eloff J.H.P. , M.S. Olivier, "An overview f image???? steganography", http://mo.co.za/openistegoverview.pdf, on January 2009.
[6]Diop, S .M Farssi, O. Khouma, H. B Diouf, K .Tall, and K .Sylla, “New Steganographic scheme based of Reed-Solomon codes, International Journal of Distributed and Parallel Systems (IJDPS)”, Vol.3, Issue.2, 2012.
[7] M. Sutaone and M. Khandare, “Image based steganography using LSB insertion technique”, in Conference on Wireless, Mobile and Multimedia Networks, 2008. IET International, Beijing, pp.146 – 151, 2008.
[8] N. F. Johnson and S. Jajodia, “Exploring steganography, seeing the unseen”, IEEE Computer Magazine, Vol.31, Issue.2, pp.26-34, 1998.
Downloads
Published
How to Cite
Issue
Section
License

This work is licensed under a Creative Commons Attribution 4.0 International License.
Authors contributing to this journal agree to publish their articles under the Creative Commons Attribution 4.0 International License, allowing third parties to share their work (copy, distribute, transmit) and to adapt it, under the condition that the authors are given credit and that in the event of reuse or distribution, the terms of this license are made clear.




